Innovative Project Showcase
Phishing Campaign Sim using Gophish
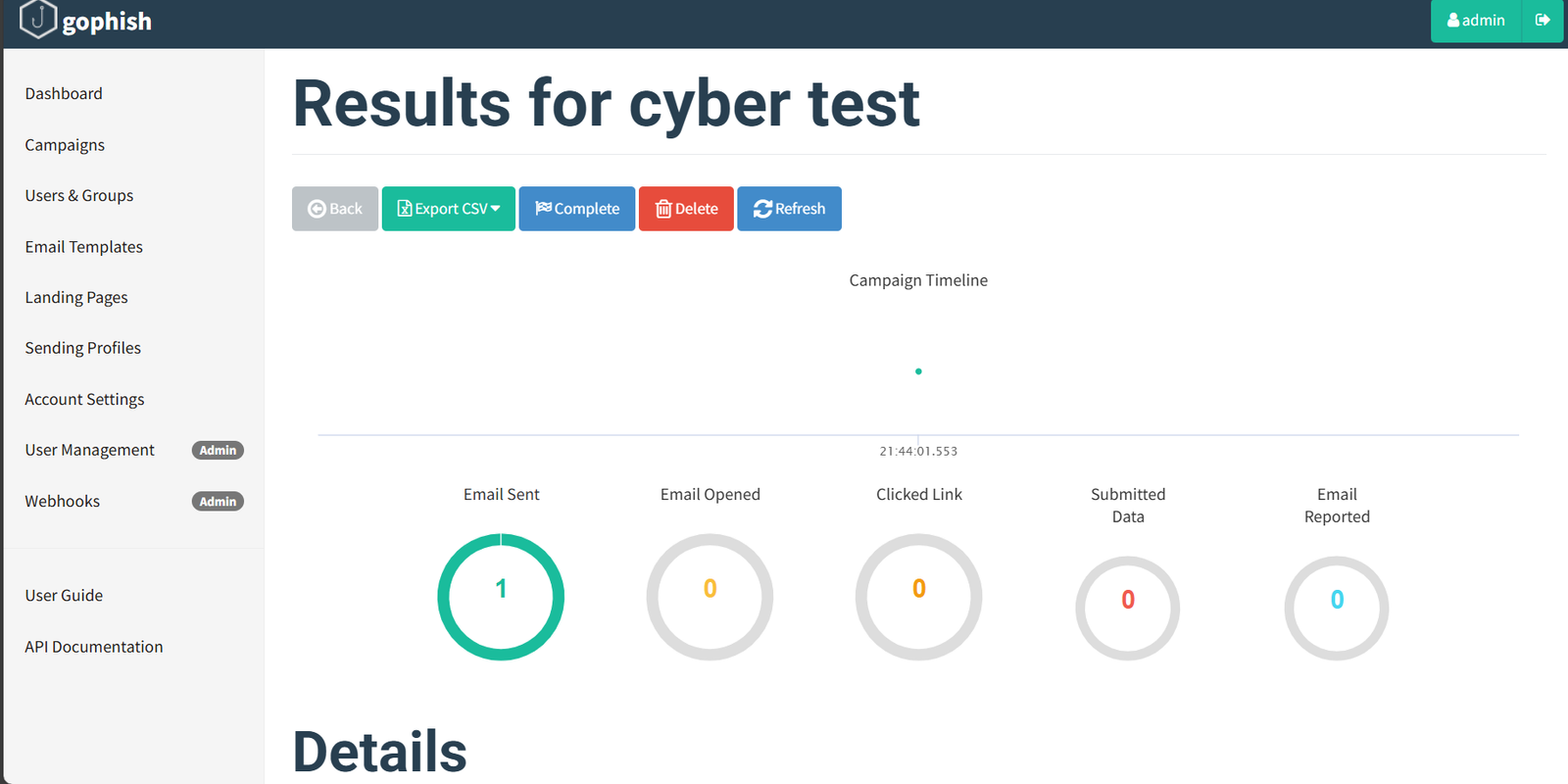
I ran a phishing simulation using the Gophish application to assess the susceptibility of users to phishing attacks. The simulation involved crafting a realistic email campaign that mimicked a legitimate communication, such as an official notification or a security alert, and sent it to a group of participants. The email contained a link designed to harvest credentials or prompt a malicious download if clicked. Gophish allowed me to track the success rate of the campaign by monitoring click rates, submissions, and other interactions, providing valuable insights into how vulnerable users were to phishing attempts and offering an opportunity to strengthen security awareness.
Network Vulnerability Detection System
I’ve implemented a network vulnerability scanning tool that not only detects potential security risks but also performs comprehensive vulnerability audits. The tool successfully identified 14 vulnerabilities (2 low, 7 moderate, 5 high) in the test environment, demonstrating its effectiveness in strengthening network security posture.
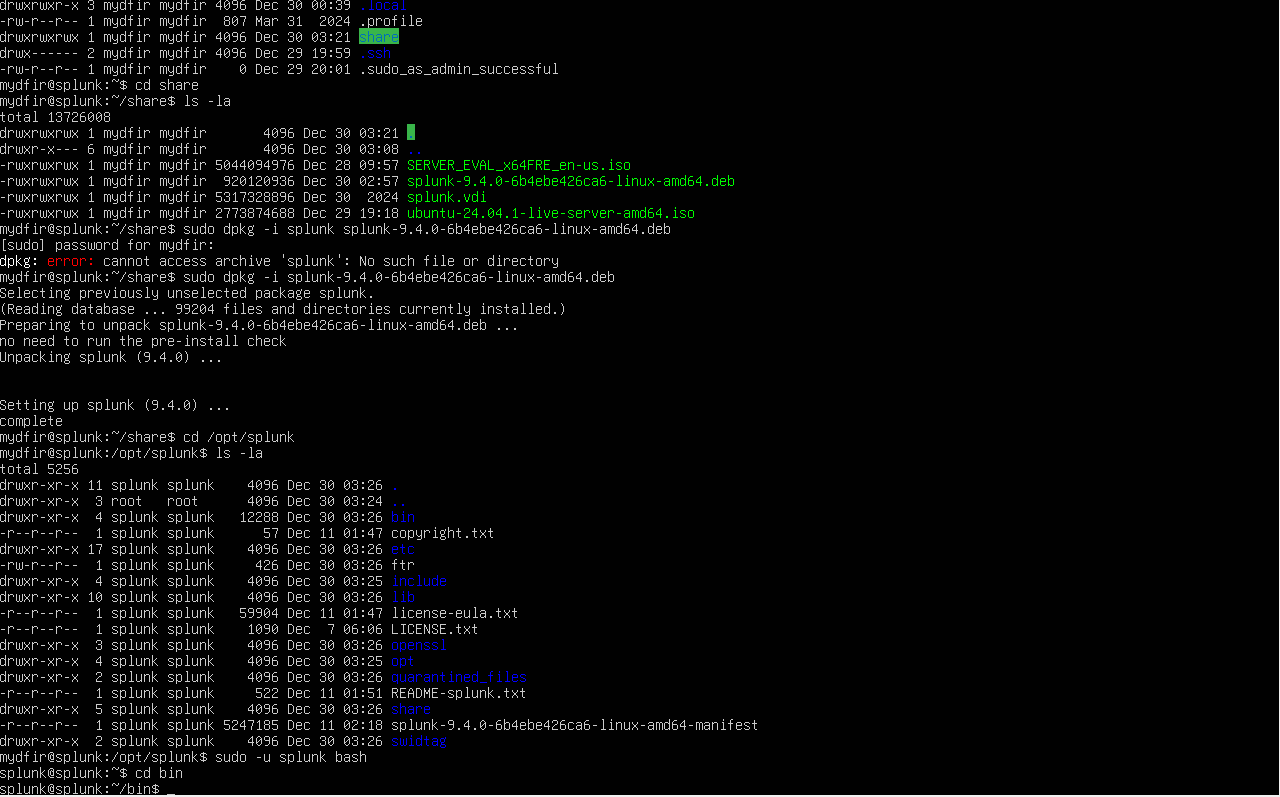
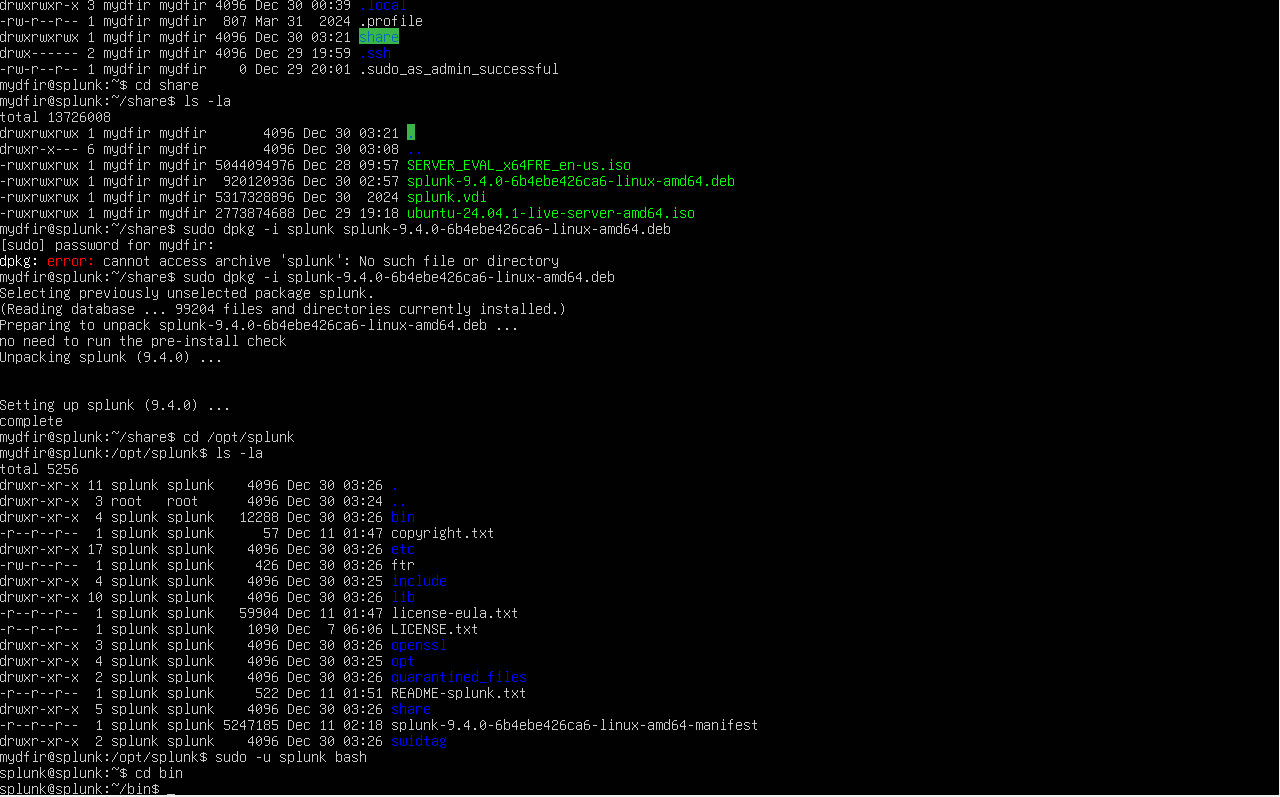
Splunk Server and Configuration
I installed and configured Splunk server to collect, index, and analyze machine data for monitoring and security purposes. First, I downloaded the appropriate version of Splunk for my system and ran the installation process, following the prompts to complete the setup. After installation, I configured Splunk by setting up the necessary configurations for data inputs, specifying the log sources, and defining indexers for data storage. I also set up user roles and permissions to manage access and ensured that the system was properly integrated with any other relevant tools or data sources for efficient data aggregation. Finally, I tested the installation by performing searches and visualizing the data to ensure everything was running smoothly.
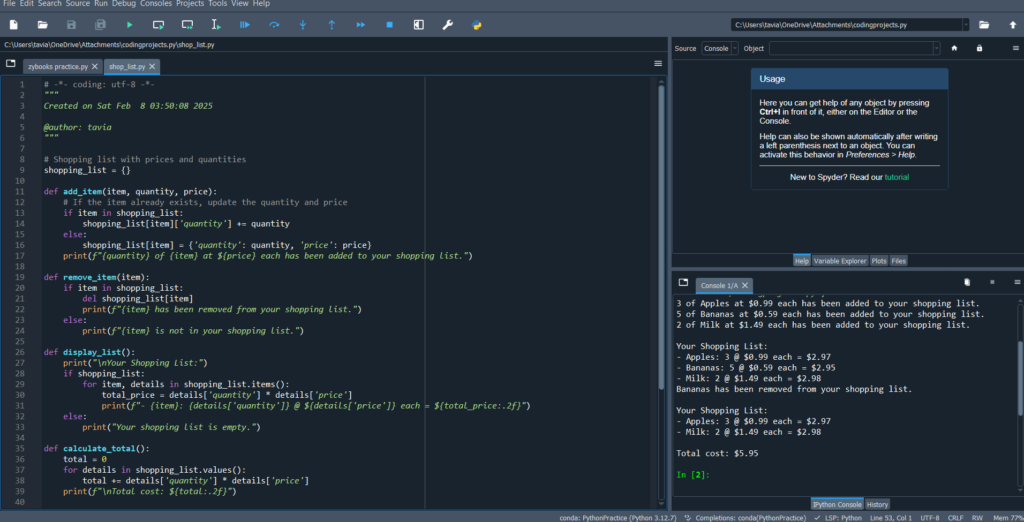
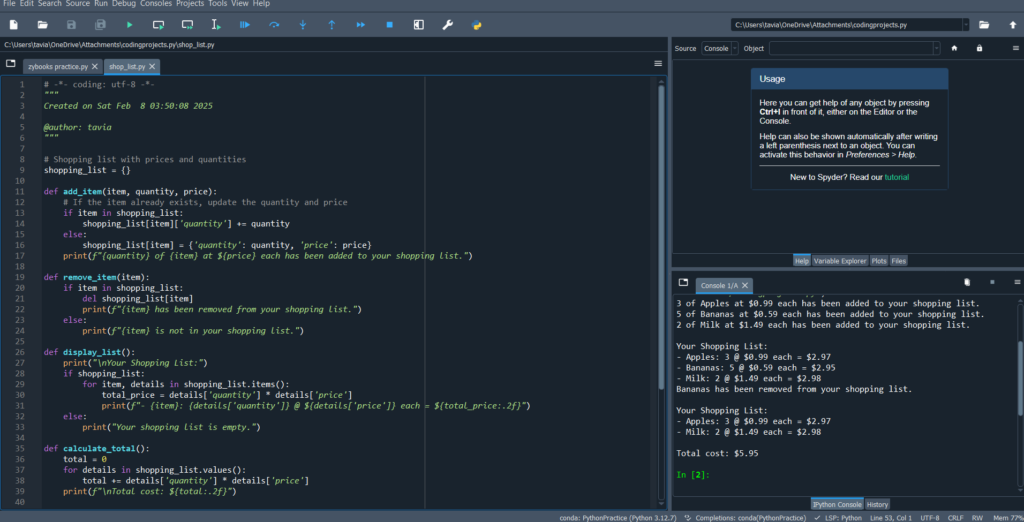
Shopping list Application: Python
This shopping list code in Python is designed to help you create, manage, and process a shopping list with item quantities and prices. It uses basic Python data structures like lists and dictionaries, as well as loops, functions, and conditional statements to handle various operations.
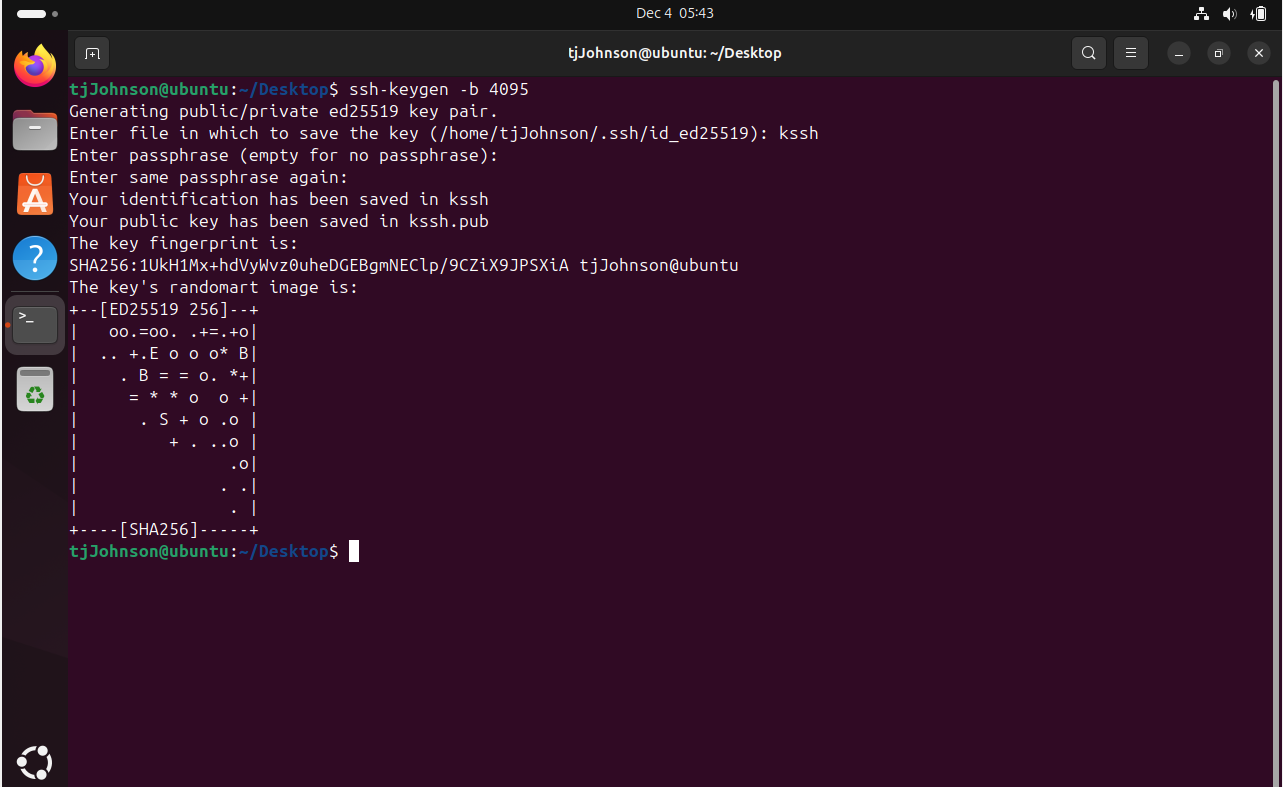
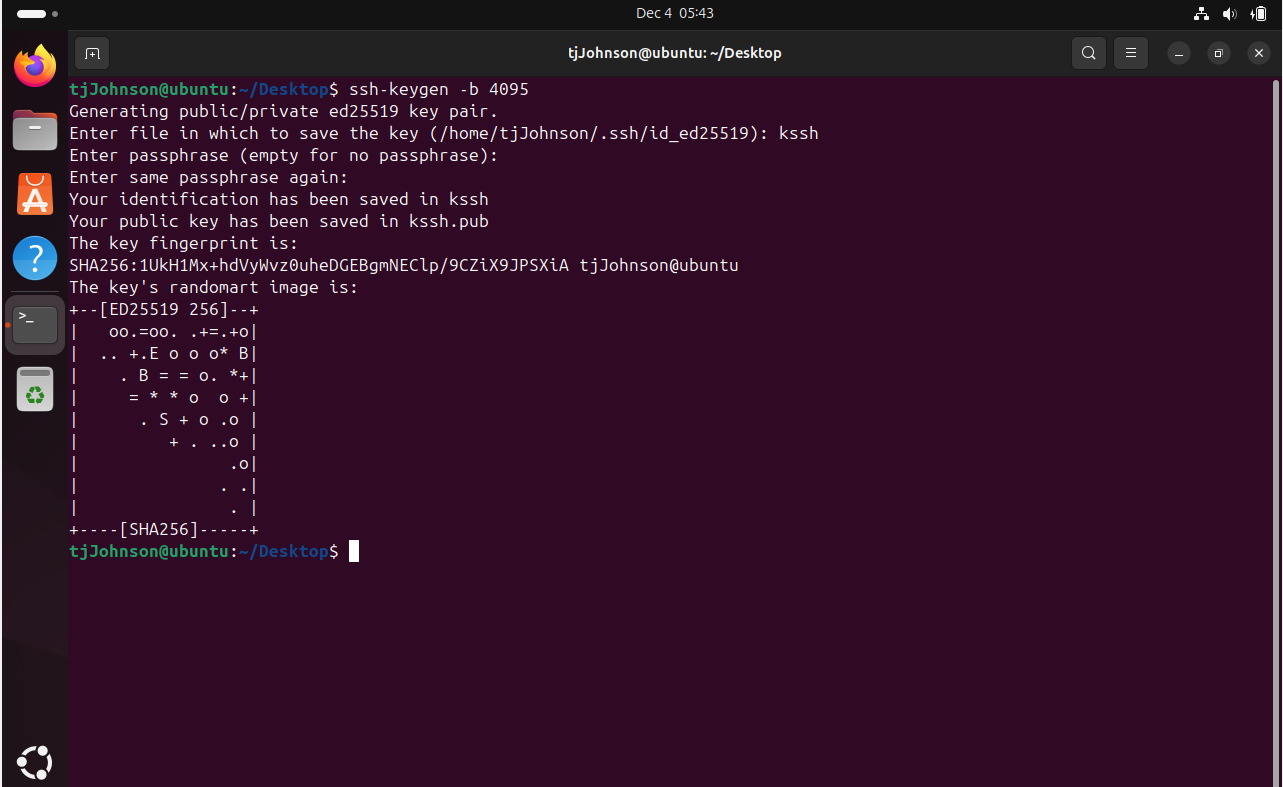
Creating public/private authentication keys in linux
Here I set up an Ubuntu Linux server! Created a new user account and fortified my network with secure public and private keys.
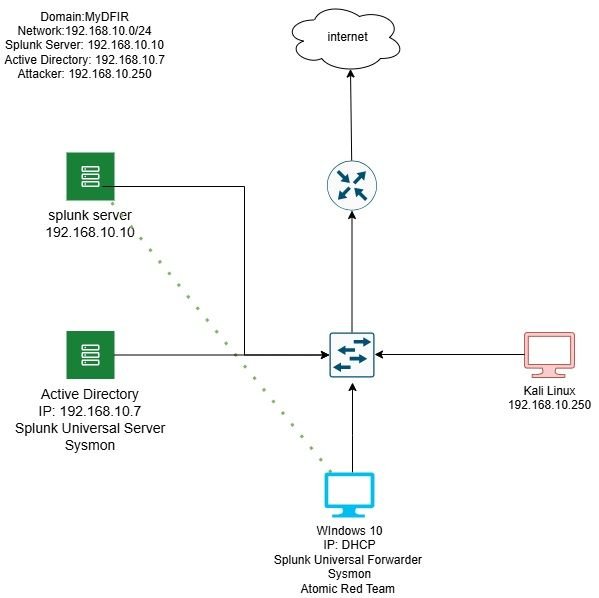
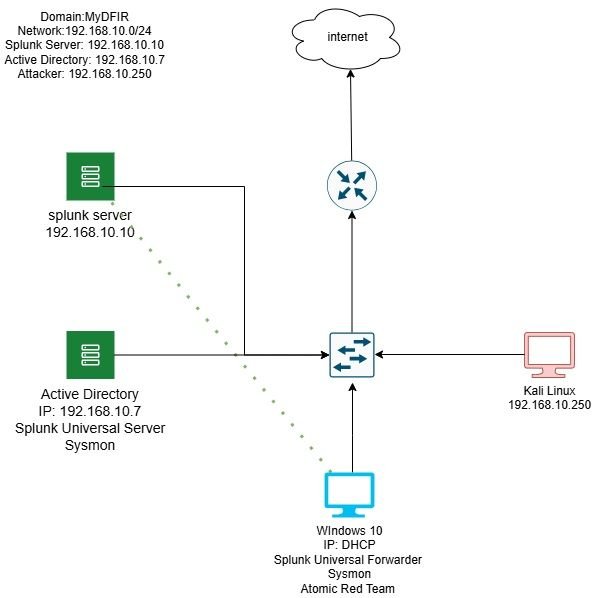
I set up an Active Directory home lab, seamlessly forwarding all data to a Splunk server via SSL!
This hands-on experience not only enhanced my skills in network security but also deepened my understanding of data management and analysis. Looking forward to leveraging these insights in future projects!
Project Showcase
Explore my diverse portfolio highlighting innovative projects and creative solutions across various domains.